Context :
- Poorly secured infrastructure
- Need to detect intrusion on DC
- Need to monitor actions during NWH
- Time constraint < 24 Hrs to setup solution
Solution :
- Dump all the server network traffic (ingress + egress) from and to a separate location
- Set up a quick and dirty shadowing script to monitor every action of any intruder on the server in real time
The first requirement depends on the infrastructure, in this case, everything was virtualised under VMWare ESXi, but it would be as equally doable under Hyper-V.
If the infrastructure was physical, i would think about either port mirroring if you have access to the L2 network, but that could definitely be tedious and costly to set up depending on the situation, or the cheap solution would be to spin a new machine that would remotely execute tcpdumps from the server.
The only problem with the latter solution, is that you would need to hide the tcpdump process from the attacker which is very much possible, but would require some extra time if you don’t have it already at hand.
Set up ESXi traffic dump
In order to do this, you first need to enable SSH access from the ESXi host, then the process is the following :
List all vswitch port numbers / VM association (similar to an ARP table) : net-stats -l
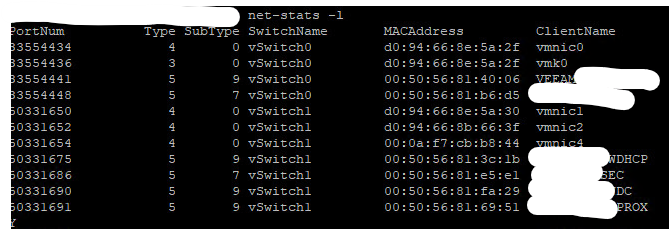
Dump the egress traffic from the DC switch port to a temporary pcap file : pktcap-uw –switchport XXXX -o /tmp/dc-out.pcap
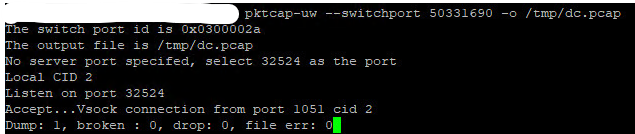
Dump the ingress traffic from the DC switch port to a temporary pcap file : pktcap-uw –switchport XXXX –dir 1 -o /tmp/dc-in.pcap
Shadowing script
I created this little script in addition, to automate the following :
- Monitor every session currently opened in the server (5 sec. refresh time but it can be changed ofc)
- Create a shadow rdp session on every newly opened session
The script is available in my github.
There are 2 versions to it attended vs unattended.
Attended version plays a little sound everytime a new session is opened, and expects a physical person to execute the shadow rdp command on the target session.
Unattended version is autonomous, and can be left to run on it’s own, it will automatically open a shadow rdp session on every newly created one allowing to set up a recording program on the physical or virtual machine, from which secops team is running the surveillance. You will need to run the recording program on your own, but this will spare you the hastle of having to be present.
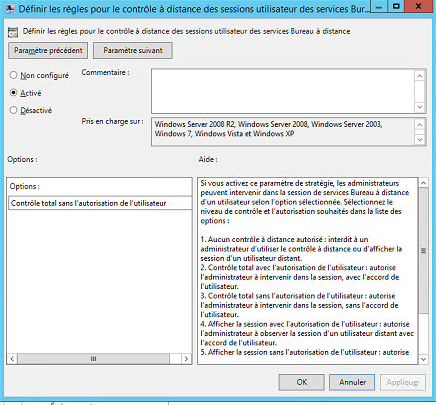
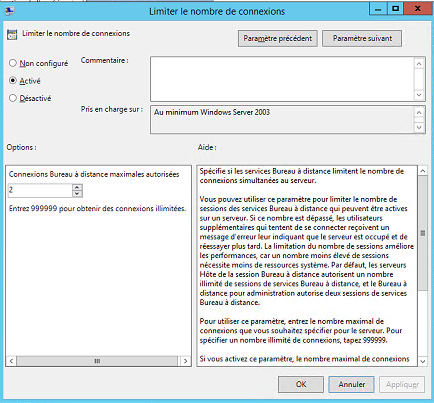
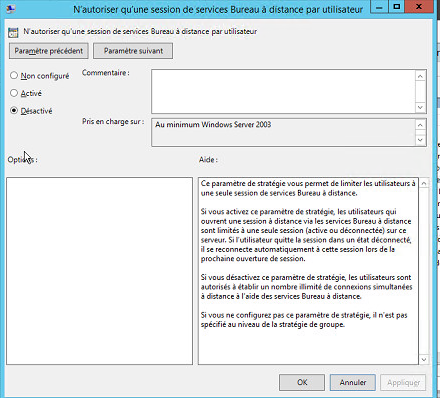
This will however require the activation of the following GPOS in the server :