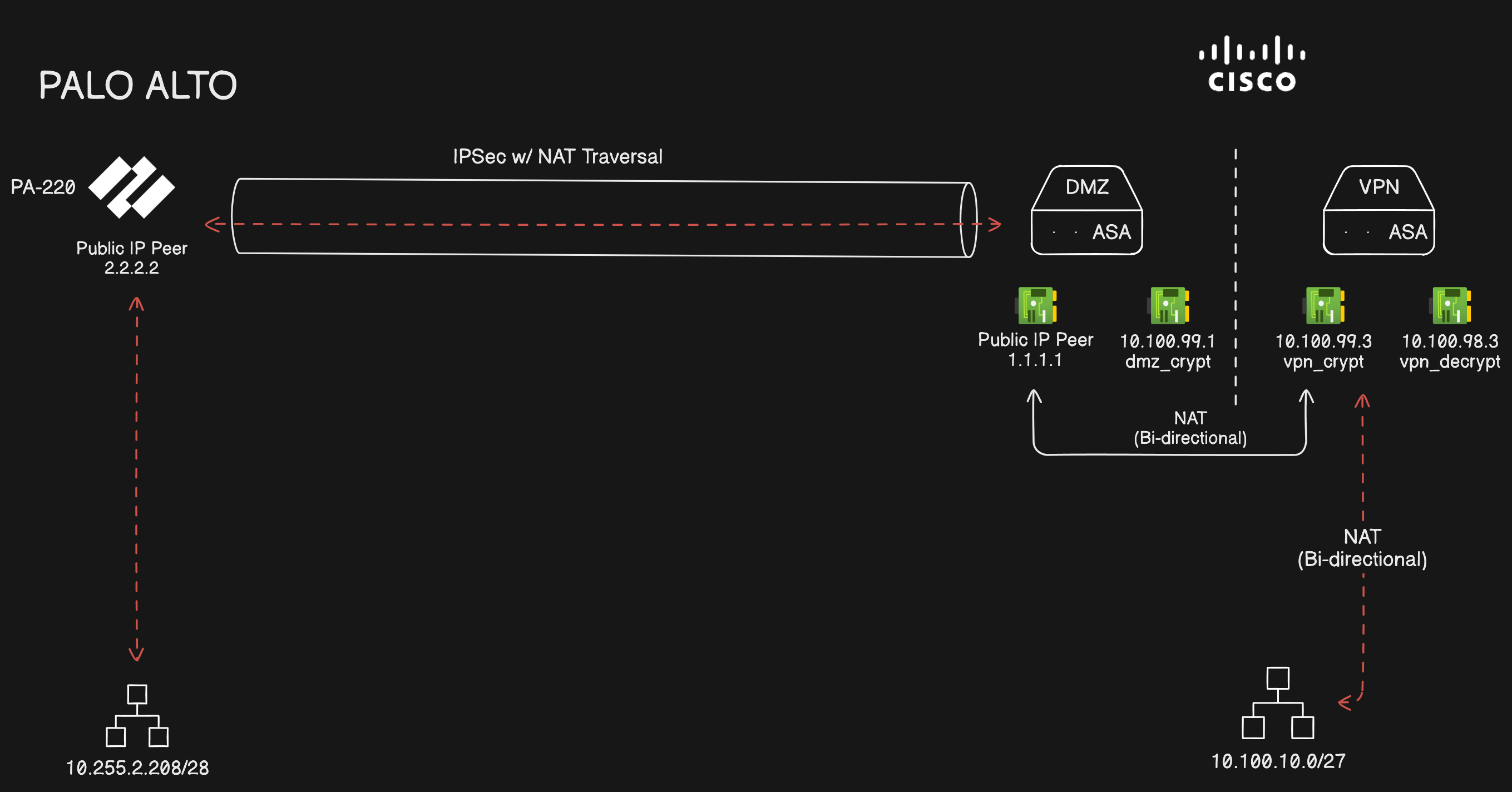
In this particular architecture, remote sites were individually configured behind a PA-220 which in turn is centralized to a maintainance center to allow for remote management and homogenization.
The central infrastructure network is routed through a double firewall configuration using 2 CISCO ASA : one for the vpn configuration holding all the tunnels, and the other for internet communications (DMZ).
My goal here was to allow a subnet within the central infrastructure (10.100.10.0/27) to remotely access machines located within the remote site (10.255.2.208/28).
Now this might not seem obvious from only looking at the subnet ranges themselves which are not overlapping, however what about the firewall routes ?
Turns out the internal network interface of the PA-220 are configured with a /8 mask meaning that any traffic incoming from it’s LAN will be routed back to it, it will never go through the tunnel routes, even after declaring a new route specifically for the 10.100.10.0/27 remote network to go through the IPSEC tunnel.
In this particular instance, LAN routing will take precedence over any other form of routing.