
Useful Tips :
Remember that a lot of commands can be done or undone with the no keyword appended before it, likewise most commands can be abreviated.
Show ip routes, show only bgp routes
1
2
sh ip ro
sh ip ro bgp
Show all interfaces, enter the configuration terminal, edit the interface and turn it on :
1
2
3
4
5
6
show ip int
conf t
int FastEthernet 1/0
ip addr 1.1.1.1 255.255.255.0
no shutdown
exit
Ping from a specific interface (loopback 0)
1
ping 1.1.1.1 source lo0
Showing, editing and deleting an ACL
1
2
3
4
show access-list 1
conf t
access-list 1 permit 1.1.1.1
no access-list 1
Interior Gateway Protocol
Let’s quickly demonstrate how to set up RIP and OSPF on a running topology.
We will chose RIP as an IGP for ASN 65003, between R13 and R11
Then we’ll interconnect R10 with the rest of the already established OSPF network in ASN 65001
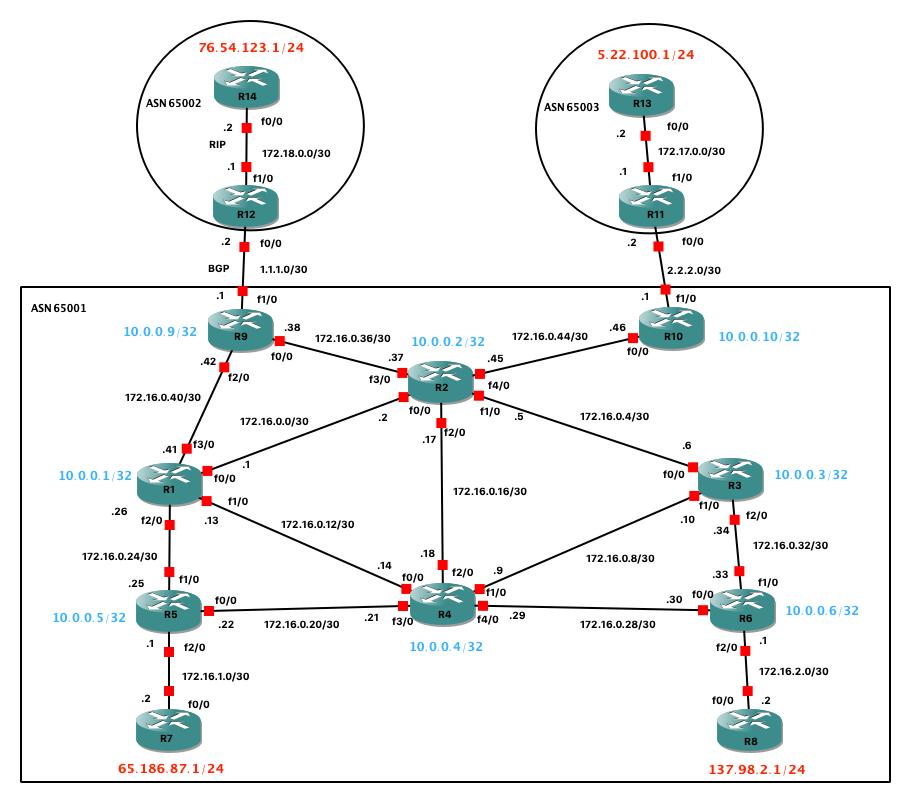
In it’s most basic form RIP can be established as easily as :(duplicate on R11 side)
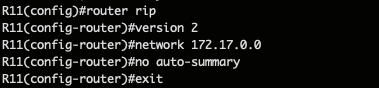
For OSPF, we need to specify the wildcard (inverted mask) as well as the area :
The previous commmands only declare the loopback network to be distributed over ospf, but we haven’t actually established any connection yet.
To do that we need to add the physical network that’s linking both routers (R10 and R2), in their ospf routing table : (on both sides)
1
2
3
router ospf 1
network 172.16.0.44 0.0.0.3 area 0
end
Exterior Gateway Protocol
BGP
The goal here is to connect the red networks without giving visibility on the ASN 65001 internal backbone.

In order to do that, we need to remember that each exterior router must do two things :
Redistribute it’s internal routes (OSPF/RIP) into the external protocol (BGP)
Redistribute it’s external routes (BGP) inside the internal network (OSPF/RIP)
It’s crucial to understand that an ip connection requires both ends to know about each others ip. The best way to check if that’s really the case is by verifying the routing table of both endpoints. Most connectivy issues (e.g ping timeout) stems from the absence of the corresponding route to a received packet’s source ip. A typical “debugging” workflow would encapsulate running tcpdump on the receiving end, checking if the packet arrives (check the source ip and timestamp), then verifying if that source ip’s network figures in the routing table.
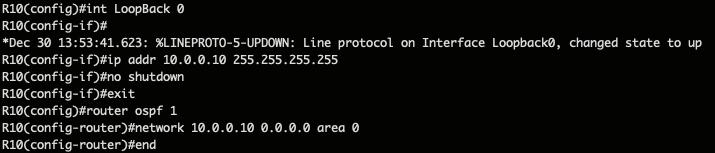
First let’s set up BGP inside R12 and R9 respectively :

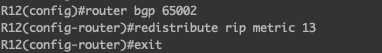
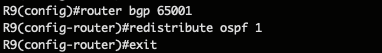
Then we must redistribute the internal network for each BGP router as stated previously :
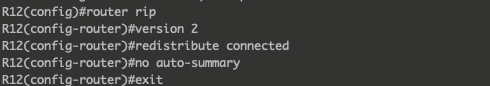
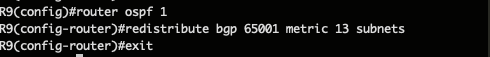
And the reverse, redistributing the external network for each :
Now we need to restrict the visibility of area 0 internal routes (172.16.0.xx/30, 10.0.0.xx/32)
This is easily done by creating an ACL and setting it as a distribute-list for the corresponding neighbor inside the bgp router :
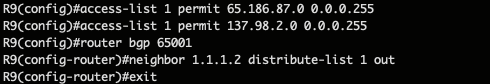
Note: Remember that an ACL will implictly deny all traffic that is not explicitly allowed.
Interconnecting BGP
In order to enable ASN 65002 and ASN 65003 for communication, we need to make sure that we’re redistributing a special type of OSPF traffic called : external type 1/2
Basically the traffic that’s being redistributed from BGP into OSPF is categorized as external, and will not be redistributed automatically into an other BGP router unless we explicitely declare it.
A quick way to verify which external ospf type is being used, would be sh ip ro ospf
The redistribution itself can be carried with :
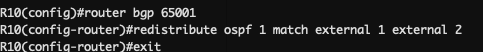
For instance R10 learned about R12 and R14 through the redistribution of R9’s BGP routes into OSPF, so for R10 (as for any other router connected to the same OSPF area than R9), these routes will be tagged as external and needs to be redistributed using the previous command.
